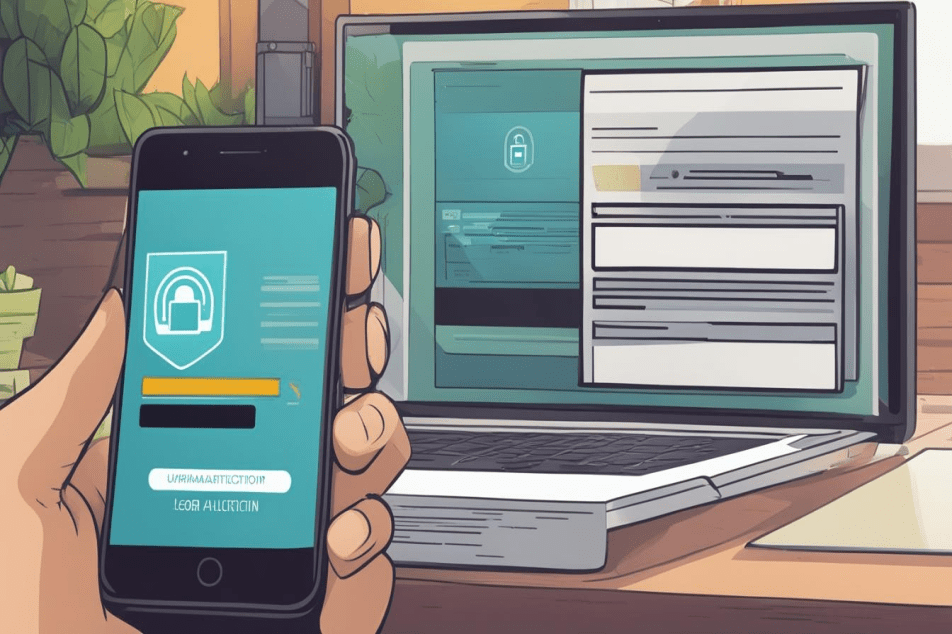
In the digital realm, where cyber threats are as common as the devices we use, two-factor authentication (2FA) serves as a critical safeguard for your online identity. By introducing a secure login procedure that goes beyond a mere password, 2FA ensures that your accounts enjoy strong authentication protection.
This isn't just about reinforcing your digital fortress; it's about adopting a proactive stance on cyber security. Google's 2-Step Verification exemplifies how adding this robust layer can be seamless and user-friendly.
Strengthen your online security by implementing a system in which your phone serves as a key to your account. With this approach, even if your password ends up in the wrong hands, two-factor authentication (2FA) ensures that your data remains inaccessible.
The Necessity of Enhanced Security Measures in the Digital Age
As you embark on your daily digital activities, it's important to recognize that strong passwords alone are no longer the bastion of cyber security. Cyber threats lurk around every corner, and with multi-factor authentication (MFA), you can significantly bolster your defense against unauthorized access.
Hackers are continuously developing sophisticated methods to compromise your online accounts. Phishing scams, where attackers masquerade as legitimate entities to purloin your credentials, and password breaches stemming from large-scale data leaks, show that passwords are no longer impervious shields.
Multi-factor authentication emerges not just as an added feature, but a fundamental necessity. By necessitating an additional form of verification, 2FA ensures that the keys to your digital kingdom don't simply lie in the hands of anyone who has guessed or stolen your password.
Here's how two-step verification can upgrade your cyber security:
- After you input your password - something you 'know' - two-step verification requires you to present a second factor - something you 'have' such as a mobile device for receiving one-time passcodes or something you 'are' like a fingerprint or a retina scan.
- This added layer comes in various forms, from one-time passcodes sent to your phone to token authentication devices and biometric verifications - all serving as a double-check of your identity.
- Token authentication, particularly, offers a tangible security asset, a physical device such as a USB key that you must possess to gain access - an effective deterrent to remote cyber intrusions.
- For even stronger protection, security keys that employ encryption offer the pinnacle of personal data safety, making them the gold standard in multi-factor authentication.
It is crucial to prioritize the implementation of two-step verification on accounts that contain sensitive information, such as your bank, email, and social media profiles. Additionally, it is highly recommended to extend this essential security measure to all aspects of your digital presence.
As you consider enhancing your personal or organizational cyber security practices, remember that the goal of multi-factor authentication isn't simply to create hurdles but to build a resilient barrier between your data and potential intruders. Investing a little time now in setting up 2FA can save you from the much larger headache of dealing with the fallout of hacked accounts or compromised data in the future.
How Two-Factor Authentication Fortifies Your Online Defenses

Understanding how 2FA operates and the different options available to use it can bolster your online defenses significantly.
Understanding the Mechanism Behind 2FA
At its core, two-factor authentication augments security by incorporating a second verification step during the login process. This means that even if a hacker were to discover your password, they would still be blocked without the second form of authentication, be it a physical token, a temporary code, or a biometric identifier.
By leveraging something you have or something you are, 2FA ensures an extra layer of defense, keeping unauthorized users at bay.

Various Types of Two-Factor Authentication Tokens
The diversity of token authentication options caters to different preferences and security needs. Common types include physical security keys that plug into a USB port or use NFC to establish a connection, and mobile device prompts or messages that provide a one-time code.
Software solutions like Google Authenticator generate time-sensitive codes that are highly resistant to interception by cybercriminals, adding to the robustness of your protective measures.
Step-by-Step Guide to Activating 2FA
Activating two-factor authentication across your various accounts can appear daunting, yet the process is straightforward.
Start by accessing the security settings of your chosen platform — be it Google, Apple ID, or another service provider. Look for the 2FA option and follow the provided setup instructions, which usually involves linking a trusted device or phone number to your account.
Once set up, you'll have the confidence that your accounts are defended with an added security layer, giving you peace of mind in your online activities.
In the face of escalating cyber threats, two-factor authentication (2FA) has emerged as a fundamental component of cyber security strategies. Providing a secure login protocol, 2FA requires more than just a password to confirm your identity, thus offering strong authentication against potential breaches.
How do you think implementing two-factor authentication (2FA) can enhance online security in the face of prevalent cyber threats?